Your Guide to NIST Cybersecurity Certification
Let's get one thing straight right from the start: there isn't one single, official "NIST cybersecurity certification" that you can get directly from NIST. It just doesn't exist. When you hear people talking about it, what they really mean are credentials from other organizations that prove you've mastered the principles within the world-renowned NIST Cybersecurity Framework (CSF).
So, What Exactly is NIST and Why Does it Matter in Cybersecurity?
Think of the NIST Cybersecurity Framework as a universal blueprint for building a strong, resilient organization in the digital age. It’s not a strict, unbending rulebook. Instead, it’s a voluntary set of guidelines, standards, and best practices that has become the gold standard for a reason. Its whole purpose is to help everyone—from a local startup to a massive federal agency—get a handle on managing and reducing their cybersecurity risks.
Learning these standards is about more than just passing an exam. It’s about learning to speak the common language of security. This is the language used in boardrooms and server rooms alike, across both the public and private sectors. Mastering it is a massive advantage for anyone looking to build a serious career in this field.
The framework's real power lies in its adaptability. It gives organizations a structured but flexible way to:
- Describe where they currently stand with their cybersecurity.
- Identify and shield their most important systems and data.
- Define a target for where they want to be.
- Prioritize the steps needed to bridge that gap.
The Blueprint for Modern Security
At its heart, the NIST Cybersecurity Framework provides a high-level, strategic view of how an organization manages its cybersecurity risk.
 Image
Image
The framework is built around five core functions—Identify, Protect, Detect, Respond, and Recover. These create a continuous cycle for managing and improving security over time. The latest update, CSF 2.0, even added a crucial sixth function: Govern. This addition officially recognizes what many experts have known for years: cybersecurity isn't just an IT problem; it's a major source of enterprise-level risk that needs executive oversight.
This approach is so effective because it’s both thorough and practical. Its influence is huge. For example, the Office of Management and Budget mandates that all U.S. federal agencies use NIST standards for their non-national security systems. This isn't just a suggestion; it's a requirement that shows how deeply NIST shapes security practices everywhere.
To give you a better idea of its reach, here's a quick breakdown of NIST's role in the cybersecurity world.
Key Areas of NIST's Cybersecurity Influence
| Area of Influence | Description | Primary Audience |
|---|---|---|
| Framework Development | Creates and maintains the Cybersecurity Framework (CSF) as a voluntary guide for risk management. | All organizations, both public and private. |
| Federal Standards | Develops mandatory standards and guidelines for U.S. federal agencies (e.g., FIPS, SP 800-series). | U.S. federal government agencies and contractors. |
| Cryptography | Sets the standards for cryptographic algorithms and modules used to protect sensitive information. | Government, financial services, tech companies. |
| Emerging Technologies | Researches and provides guidance on the security of new tech like AI, IoT, and quantum computing. | Researchers, innovators, and early adopters. |
This wide-ranging influence, from setting federal policy to guiding work on AI security, is exactly why understanding NIST is no longer optional for serious cybersecurity professionals. If you're interested in the nitty-gritty, you can read more about how NIST develops these crucial guidelines on their official site.
Understanding the Five Core NIST Functions
To really get a handle on what a NIST cybersecurity certification is all about, you need to understand the framework's operational heartbeat: its five core Functions. These aren't just steps on a checklist. Instead, think of Identify, Protect, Detect, Respond, and Recover as a continuous, looping cycle for managing and strengthening an organization's security.
A great way to visualize this is to think about how you'd protect a modern city. Each function plays a distinct, critical role in keeping that city safe, running, and resilient.
Identify: Know Your Most Critical Assets
Before you can even think about protecting a city, you have to know exactly what you're protecting. This is the Identify function. It’s like creating a detailed map of all the city's critical infrastructure—from the power grid and water systems to hospitals and communication networks.
In the world of cybersecurity, this means getting a deep, foundational understanding of your business context. You need to know:
- Your Assets: What are the most vital pieces of hardware, software, data, and systems that keep your business running?
- Your Risks: What specific threats and vulnerabilities could actually impact those assets?
- Your Environment: How do your business goals and supply chain partners shape your overall risk profile?
Without this comprehensive inventory, your security efforts are basically just shots in the dark. The Identify function ensures your entire strategy is built on a solid foundation of self-awareness.
Protect: Build Strong Defenses
Once you've got your city mapped out, it's time to build its defenses. This is the Protect function. You’re essentially constructing the city walls, training the guards, setting up access checkpoints, and running public safety campaigns. The whole point is to make it as tough as possible for threats to get through.
For a business, this translates into putting safeguards in place to guarantee the delivery of your critical services. It’s all about being proactive. Key activities here include:
- Managing who has access to sensitive data and systems.
- Running regular security awareness training for every single employee.
- Implementing solid data security measures, like encryption and reliable backups.
- Maintaining protective tech like firewalls and endpoint security software.
Detect: Set Up City-Wide Alarms
Let's be realistic: no wall is perfect. That's why every smart city needs a city-wide alarm system. The Detect function is your network of surveillance cameras, motion sensors, and watchtowers that spot trouble the second it appears. This lets you identify a potential breach long before it causes any real damage.
In the digital realm, this means having systems that can discover a cybersecurity event as it’s happening. It’s all about continuous monitoring of your networks and systems to spot anomalies and potential threats in real time.
Key Takeaway: The goal of the Detect function isn't just to find breaches after the damage is done. It's about spotting the subtle signs of an attack that's in progress, which allows for a much faster and more effective response.
Respond: Execute a Clear Emergency Plan
When an alarm finally goes off, chaos is your worst enemy. The Respond function is the city’s detailed emergency action plan. It's the playbook that firefighters, police, and medical teams follow the moment a crisis hits, making sure the reaction is coordinated, efficient, and effective.
Likewise, your organization needs a well-rehearsed plan for what to do when an incident is detected. This involves:
- Response Planning: Having a clear, actionable incident response plan ready to go.
- Communication: Knowing exactly who to tell and when, both inside and outside the company.
- Analysis: Quickly digging into the incident to figure out its scope and impact.
- Mitigation: Taking immediate action to contain the threat and stop it from spreading.
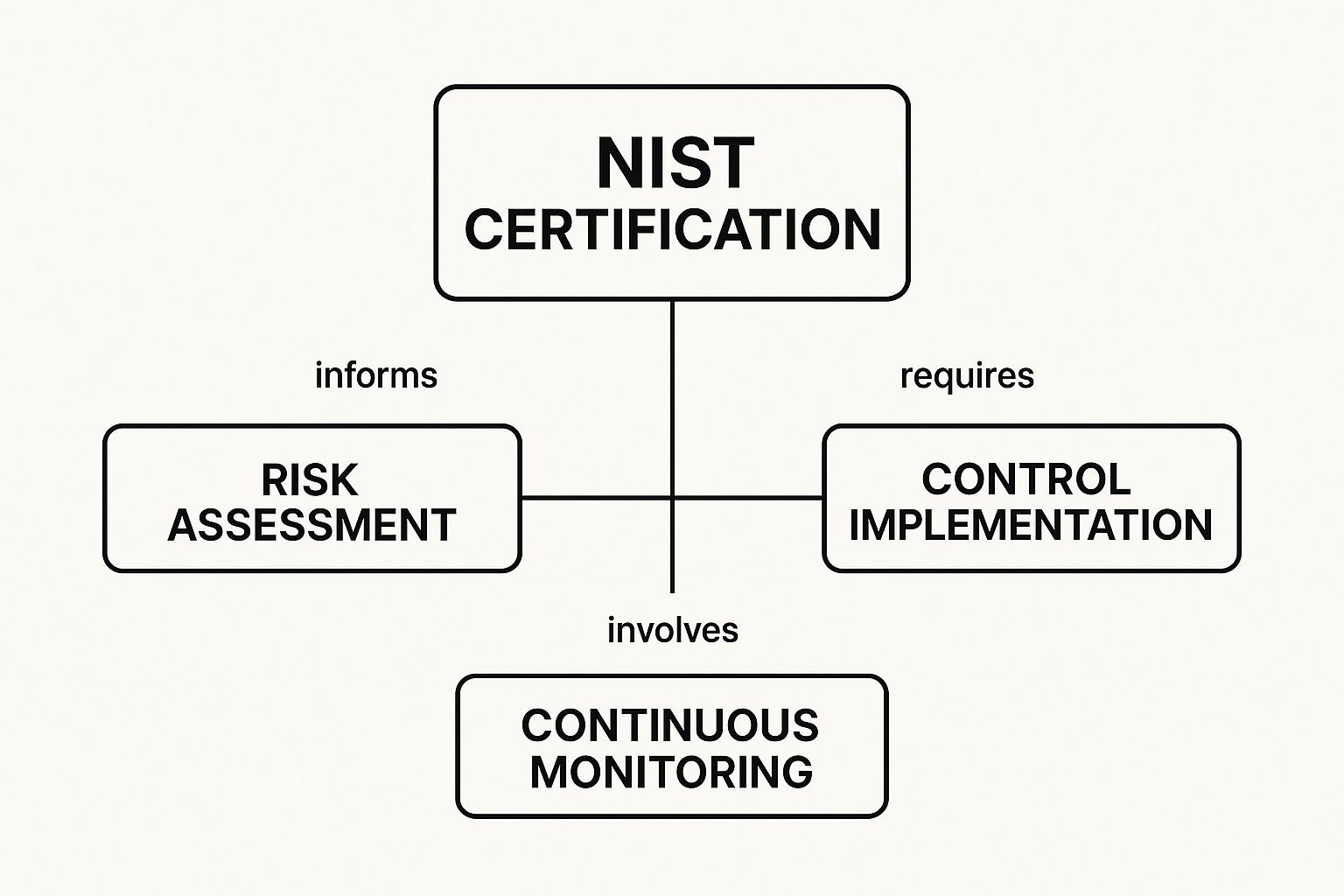
This infographic shows how obtaining a NIST certification is closely tied to the continuous loop of risk assessment, control implementation, and ongoing monitoring.
 Image
This visualization highlights that certification isn't a one-time event but a commitment to a cyclical process of managing security.
Image
This visualization highlights that certification isn't a one-time event but a commitment to a cyclical process of managing security.
Recover: Rebuild and Get Back to Business
After the crisis has been contained, the work is far from over. The Recover function is the city's strategy for rebuilding damaged infrastructure, restoring essential services, and getting life back to normal. It’s all about resilience and continuity.
This directly translates to having a plan to restore any systems or services that were knocked out by a cybersecurity event. The primary goal is to return to normal operations as quickly and safely as possible, all while learning from the incident to build stronger defenses for next time.
Of course, even the best framework can fail without a skilled team to execute these functions. The global cyber skills gap has widened, with a majority of organizations reporting significant shortages of qualified professionals. This directly impacts their ability to implement NIST standards effectively. You can explore more about this challenge in the World Economic Forum's latest report.
Making Sense of the NIST Risk Management Framework
 Image
Image
If you think of the Cybersecurity Framework (CSF) as the high-level blueprint for security, the Risk Management Framework (RMF) is the detailed, step-by-step construction plan. It’s the practical “how-to” guide for building, securing, and maintaining a system, especially for any organization that deals with the U.S. federal government.
While the CSF is a fantastic, voluntary guide for just about anyone, the RMF is a much more formal, structured process. In fact, it's mandatory for federal agencies and their contractors. If you're aiming for a NIST cybersecurity certification, you'll need to know the RMF inside and out, as it dictates exactly how security controls get picked, put in place, and watched over.
Let's use an analogy to make this stick: getting a commercial pilot's license. It's not a single test; it's a rigorous journey with clear stages, each one building on the last. The RMF works the same way.
The Seven Steps of the RMF
The RMF is a seven-step loop designed to weave security and risk management directly into a system's development from day one. This ensures security is a core component, not just something bolted on at the end when it's often too late.
-
Prepare: This is the groundwork. For our future pilot, this is ground school—learning the physics of flight, weather systems, and FAA regulations. In the RMF, this means getting your organization ready to make smart, consistent risk-based decisions.
-
Categorize: A pilot needs to know if they're flying a small prop plane or a jumbo jet. The risks are completely different. Similarly, you must categorize your information system based on the potential damage if its confidentiality, integrity, or availability were compromised. This tells you how tough your security really needs to be.
-
Select: Based on the type of aircraft, a pilot chooses specific checklists and safety gear. In the RMF, you select a starting set of security controls from the extensive catalog in NIST Special Publication 800-53. You then fine-tune these controls to fit your specific system and environment.
Expert Insight: The RMF is not a one-size-fits-all checklist. The 'Select' step is where the real expertise comes in. It’s about tailoring the controls to address the actual risks your organization faces, so you don't waste money on protections you don't need or leave dangerous gaps in your defense.
- Implement: This is the pilot's pre-flight check, where they physically walk around the plane and follow procedures before takeoff. For your system, this means installing, configuring, and documenting the security controls you selected. Clear documentation here is non-negotiable.
From Setup to Constant Vigilance
The RMF doesn't just stop after you've flipped all the switches on. The next three steps are all about verification and staying alert—concepts absolutely critical for anyone wanting to pass a NIST cybersecurity certification exam.
-
Assess: Think of this as the pilot's flight test. An examiner gets in the cockpit and evaluates their skills under pressure. In the RMF, an independent assessor comes in to verify that your security controls are in place, working correctly, and achieving the security you intended. This provides the confidence that the system is truly secure.
-
Authorize: After the pilot aces their flight test, the FAA grants them a license, formally authorizing them to fly. For a system, a senior leader known as the Authorizing Official (AO) reviews all the evidence from the assessment and makes a final, risk-based decision. If they're satisfied, they grant an Authorization to Operate (ATO).
-
Monitor: A pilot's license isn't good forever; it requires ongoing flight hours and recurrent training to stay valid. The Monitor step is the RMF's version of that. It’s a continuous process of checking your security controls, making sure they're still effective, and adapting to any changes in the system or the threat landscape.
This disciplined, cyclical process is truly the backbone of federal information security. Getting a handle on it proves you understand how to manage risk in complex, high-stakes environments—a skill that is incredibly valuable in both government and corporate worlds.
Choosing Your NIST-Aligned Certification
Once you've got a firm handle on the NIST frameworks, the natural next step is to get a credential that proves what you know. This is where third-party certifications become so valuable—they give you a clear, official way to show your skills to employers.
But which NIST cybersecurity certification is right for you? That really depends on where you want to go in your career. Different credentials are built for specific jobs and industries. It’s a lot like choosing a medical specialty. A cardiologist and a neurosurgeon are both brilliant doctors, but their expertise is laser-focused. In the same way, certifications that align with NIST are designed for distinct career paths, whether you're aiming to be a federal compliance guru or a defense industry expert. Let's dig into some of the most respected options out there so you can find your perfect match.
For Federal and RMF Specialists
If your career goals involve working directly with U.S. federal agencies—or the contractors who support them—there’s one certification that truly stands head and shoulders above the rest.
- (ISC)² Certified Authorization Professional (CAP): This is the gold standard for professionals who live and breathe the Risk Management Framework (RMF). Earning a CAP shows you have the deep technical know-how to authorize and maintain information systems using the official RMF process. It covers every one of the seven steps, from categorizing systems all the way to continuous monitoring.
A CAP certification tells hiring managers you can expertly navigate the intricate maze of federal compliance. It immediately makes you a top contender for roles like Information Assurance Manager, System Security Officer, or IT Risk Manager. It's built for experienced pros responsible for formally accepting risk and securing government systems.
For the Defense Industrial Base
Working with the Department of Defense (DoD) means dealing with an extra, rigorous layer of security called the Cybersecurity Maturity Model Certification (CMMC). This has created a huge demand for people who understand both NIST standards and CMMC requirements.
- Certified CMMC Professional (CCP): This certification is a must-have for anyone helping organizations get ready for and pass their CMMC assessments. A CCP is qualified to join an assessment team, working under a lead assessor to confirm that a company's security controls are up to snuff for their required CMMC level.
This path is perfect for consultants, IT managers, and security pros working within the Defense Industrial Base (DIB). It proves you can take the controls outlined in NIST SP 800-171 and apply them to the specific practices the DoD demands—a critical skill for the estimated 300,000+ companies in the defense supply chain.
Key Insight: Think of it this way: CAP is broad, covering the RMF for all federal agencies. CMMC certifications, on the other hand, are hyper-focused on the unique security needs of the Department of Defense supply chain. Your choice really boils down to whether you see yourself working across the government or specializing in defense.
Comparing Popular NIST-Aligned Certifications
Making the right call takes some thought about where you want your career to go. This table breaks down the leading NIST-aligned credentials to help you see which path fits you best.
| Certification | Issuing Body | Primary Focus | Ideal Candidate |
|---|---|---|---|
| CAP | (ISC)² | RMF, Federal Information Systems | Federal employees, contractors, RMF practitioners |
| CCP | CyberAB | CMMC, DoD Supply Chain Security | DIB consultants, IT/Security managers in defense |
| CISSP | (ISC)² | General Cybersecurity Management | Security leaders, managers, architects |
| CISA | ISACA | Information Systems Auditing | IT auditors, compliance & control professionals |
At the end of the day, passing any of these tough exams comes down to dedication and having the right study plan. You need to find a method that genuinely challenges you and prepares you for the real thing. For example, you can simulate real exam conditions with HydraNode’s AI-driven practice tests at https://hydranode.ai/exam. This helps you pinpoint your weak spots and walk into the testing center with confidence.
Choosing the right certification is the first step. Mastering the material is what gets you across the finish line.
Building Your NIST Certification Study Plan
 Image
Image
Let's be honest, you can't just cram for a NIST cybersecurity certification exam and expect to pass. These aren't simple tests of memorization. They're designed to validate real-world expertise, which means you need a smart, structured approach to your preparation. A solid study plan is your roadmap—it breaks down what feels like a mountain of information into manageable, bite-sized pieces.
Your first stop should always be the source material. The official NIST publications are the undeniable truth for any exam on this subject. You'll want to start with the core Cybersecurity Framework (CSF) document itself, then dive into the more specific Special Publications that line up with your certification goals.
For instance, if you're targeting a credential centered on the Risk Management Framework (RMF), then NIST SP 800-53 isn't just recommended reading; it's absolutely essential. Think of these documents as the bedrock for everything you're about to learn.
Creating a Practical Study Schedule
Once you have the core documents, it’s time to give your learning some structure. Simply reading page after page is a recipe for burnout. The key is to break down the dense topics into smaller, more focused study blocks. A good plan is flexible and prioritizes consistent, daily progress over marathon cramming sessions.
Here’s a practical way to build your schedule:
- Map the Exam Blueprint: Every certification exam comes with a detailed blueprint or list of objectives. This is your treasure map. Use it to structure your study plan, giving more time to the domains that carry the most weight on the exam.
- Set Realistic Goals: You won't master the entire RMF over a weekend, so don't even try. Instead, set small, achievable weekly goals. For example, a goal might be, “This week, I will understand and be able to explain the 'Categorize' and 'Select' steps of the RMF,” or “I will review 20 specific security controls and their intent.”
- Mix Theory with Practice: Keep your brain engaged by switching things up. Alternate between reading the official NIST documents, watching training videos, and taking practice exams. This approach helps reinforce concepts from different angles and keeps things from getting stale.
This balanced method helps you stay motivated and ensures you're actually absorbing the material, not just letting it wash over you.
Applying Knowledge Actively
Reading about NIST concepts is one thing, but truly mastering them means rolling up your sleeves and applying what you've learned. Deep understanding comes from doing. This hands-on philosophy is what builds the problem-solving muscle you’ll need for both the exam and your career.
Key Takeaway: Theoretical knowledge is just the starting point. Practical application is what cements your expertise. Challenge yourself to use what you’ve learned in a hypothetical scenario. For example, try to outline a basic security plan for a small business using the CSF's five core functions.
This kind of active learning bridges the gap between knowing the steps of the RMF and understanding why each one is so critical. It turns abstract rules into tangible actions.
Leveraging Smart Study Tools
Finally, bring high-quality training courses and practice exams into your study routine. These tools are built to put you under a bit of pressure, shining a light on any weak spots you might have. Timed practice tests are particularly valuable, as they get you used to the rhythm and pressure of the actual exam environment.
The right prep tools can make all the difference. For anyone serious about making their study time count, HydraNode offers an AI-driven platform that provides adaptive question banks and realistic exam simulations. You can explore our plans and features at https://hydranode.ai/pricing and see how it can help you get ready.
Ultimately, a well-thought-out plan, combined with the right tools, will give you the confidence you need to walk in and ace your NIST cybersecurity certification exam.
Accelerating NIST Mastery with HydraNode
Let’s be honest: knowing the NIST frameworks in theory is one thing, but truly mastering them is another beast entirely. To pass a tough NIST cybersecurity certification exam and excel in your career, you have to close the gap between what you've read and what you can actually do. This is where modern study tools come into play, helping you shift from memorizing concepts to applying them in a meaningful way.
Think of it like having a digital co-pilot on your certification journey. Instead of just highlighting dense PDF documents for hours, you could be actively working with the material, testing your skills in a realistic setting, and getting immediate feedback on where you need to improve. This hands-on approach is what builds the deep, practical understanding that exams test for and employers are desperate to find.
From Textbooks to Hands-On Practice
If you want to master the finer points of the Risk Management Framework (RMF) or the Cybersecurity Framework (CSF), flashcards alone won't cut it. You need practice. Tools built for active learning can completely change how you prepare, making every study session more productive.
A platform like HydraNode acts as that digital co-pilot. It offers a dynamic, hands-on experience that mirrors the real-world challenges you'll face on the job. By simplifying and even automating complex compliance tasks, it becomes an incredible training ground for aspiring professionals.
For instance, look at how a modern tool can organize complex compliance information, making it far easier to understand.
What you’re seeing is a clean, structured way to manage security controls—a core responsibility for anyone working with NIST standards. It’s a world away from a cluttered spreadsheet.
Streamlining Your Learning Workflow
The path to a NIST-aligned certification means wrestling with hundreds of security controls and complex processes. Trying to manage all of that manually while also learning the principles behind it can feel completely overwhelming. An intelligent platform can streamline this entire workflow, turning a mountain of work into a manageable learning experience.
Here’s how this works for someone studying for a certification:
- Automated Documentation: Instead of getting lost in the weeds of paperwork, you can use a tool to generate compliance reports and System Security Plans (SSPs) in just a few minutes. This frees you up to focus on why these documents are so important and how they're structured.
- Visual Control Implementation: You can see exactly how security controls from NIST SP 800-53 are chosen, customized, and applied to a system. This visual link makes abstract requirements tangible and much easier to remember.
- Real-World Task Simulation: Working inside a simulated compliance environment helps you build muscle memory for the exact tasks you’ll perform every day in a cybersecurity role.
Key Takeaway: The goal isn’t just to pass an exam; it’s to become a competent professional. Using a tool that mirrors real-world compliance work gives you practical experience, which is infinitely more valuable than just memorizing facts.
Gaining Confidence and Career Readiness
At the end of the day, the best study method is one that builds genuine confidence. When you've already practiced applying security controls, generating reports, and navigating the RMF steps over and over, the exam feels more like a final review of skills you already have, not a brand-new, terrifying challenge.
This practical approach drastically reduces the chance of human error and teaches you the meticulous attention to detail the job demands. By using a platform that simplifies these complex processes, you’re not just studying for a test; you're preparing for your career. You learn to think like a seasoned security analyst, which makes you a far more compelling candidate to any hiring manager.
If you’re ready to go beyond old-school study habits and get on the fast track to a NIST cybersecurity certification, you can discover how HydraNode’s AI-driven platform supports NIST mastery and completely changes the exam preparation game.
Frequently Asked Questions
It's completely normal to have a few questions as you start digging into NIST frameworks and the credentials that go with them. This is a big topic, after all. Let's tackle some of the most common questions people ask about getting a NIST cybersecurity certification and what it really means for your career.
Does NIST Provide an Official Cybersecurity Certification?
This is probably the biggest point of confusion, so let's clear it up right away: No, the National Institute of Standards and Technology (NIST) does not hand out its own official certifications to people.
When you hear someone talk about a "NIST certification," what they're really referring to are credentials from other highly respected organizations. These certifications prove that you've mastered a specific NIST framework, like the CSF or the RMF. Think of it this way: NIST creates the blueprint (the framework), and other bodies certify the architects and engineers (the cybersecurity professionals) who know how to use it.
Good examples of this are the Certified Authorization Professional (CAP) from (ISC)² or the various CMMC credentials from the CyberAB.
Is NIST Knowledge Only for Government Jobs?
Not at all. It's true that the RMF is a requirement for U.S. federal agencies, which is where it got its start. But the NIST Cybersecurity Framework (CSF) has exploded in popularity across the private sector. Thousands of companies in finance, healthcare, manufacturing, and even retail have willingly adopted the CSF as their go-to guide for building a strong security program.
In fact, its influence is so strong that a recent Texas law offers a legal "safe harbor" to businesses hit by a data breach. The catch? They have to prove they were already maintaining a recognized cybersecurity program, with the NIST CSF being a prime example. This highlights just how critical this knowledge has become outside of government circles.
Having NIST expertise on your resume is a powerful, versatile skill that's in high demand whether you're aiming for a public sector role or a job at a Fortune 500 company.
How Long Does It Take to Prepare?
The honest answer? It really depends on your starting point and your target. Your timeline will be shaped by two main things:
- The specific certification you're after.
- Your current level of hands-on experience.
For a seasoned IT security pro, preparing for a credential like the CAP might take somewhere between two to four months of focused, consistent study. If you're newer to cybersecurity, you'll want to budget more time to really absorb the foundational concepts.
No matter your background, the best first step is to grab the official exam blueprint from the organization that offers the certification. Use that to map out a realistic study plan for your NIST cybersecurity certification journey.
Ready to stop guessing and start mastering the material you need to pass your exam? HydraNode provides an AI-powered study platform with adaptive practice questions and simulations that feel just like the real test. Start studying smarter with HydraNode.


